SSL v3.0 POODLE vulnerability
A new SSL vulnerability is doing the rounds morning, known as POODLE, or Padding Oracle On Downgraded Legacy Encryption.
POODLE is a newly disclosed vulnerability in the legacy SSL 3.0 protocol that could be exposing users of newer Transport Layer Security (TLS) encryption protocols to risk.
If exploited, the POODLE flaw could potentially enable an attacker to access and read encrypted communications.
What is POODLE?
The POODLE vulnerability relies on the existence of the old SSL v3.0 encryption within the operating system that the service is running on. SSL 3.0 is a cryptography protocol that debuted back in 1996 and has long since been superseded by TLS version 1.0, 1.1 and more recently TLS 1.2, which was officially defined in August 2008.
While SSL 3.0 is now a legacy protocol, many modern Web browsers and Web servers still support SSL 3.0 as a fall-back mechanism.
The best route of action is to remove this Encryption Protocol from the operating system leaving the much more secure TLS protocols to be used.
This, in theory, could affect any customers who use any web based services within our products that run over SSL connections.
Affected products would include…
- MDaemon (WorldClient and Webadmin)
- SecurityGateway
- MailStore Client and Outlook Addon access
- BackupAssist Multisite Manager
Am I affected? Do the test…
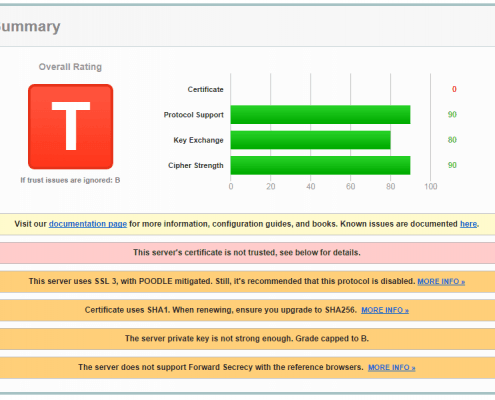
The easiest way to check if your web service is affected is to enter it here..
https://www.ssllabs.com/ssltest/analyze.html
This site will give you a clear breakdown of all the supported cryptography protocols and whether V 3.0 is available and the server is vulnerable to the POODLE attack
Don’t forget, if you repeat the test – clear the cache first using the link on the site or changes will NOT be detected.
How to remove SSL v3.0
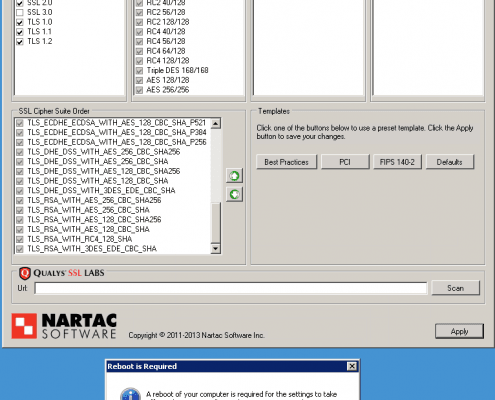
If you do appear to be affected you can then run the following tool from Nartac to select and remove SSL 3.0 from the operating system pool.
https://www.nartac.com/Products/IISCrypto/
Simply un-select the SSL 3.0 Protocol and click Apply. Please note a server reboot will be required but this must be done manually. The tool will NOT reboot the server for you.
Further reading
Eweek: http://www.eweek.com/security/poodle-flaw-found-in-legacy-ssl-3.0-encryption.html
The Register: http://www.theregister.co.uk/2014/10/14/google_drops_ssl_30_poodle_vulnerability/
Reuters: http://uk.reuters.com/article/2014/10/15/uk-cybersecurity-encryption-poodle-idUKKCN0I400920141015