Post-launch security steps to take in WooCommerce
Security isn’t something you can think about once and never again. If you don’t keep your store up-to-date, pay attention to security trends, or harden your defenses as you grow and scale, you could be putting yourself in a very vulnerable position… and also putting your customers at risk.
Because we believe the topic of security is crucial to store owners, we wanted to come back and visit this topic again, this time for those of you who already have your WooCommerce-powered site up and running. So today, we’re going to offer five intermediate level security tips for stores that have already launched.
Let’s explore a few more ways that you can make your store virtually immune to attacks, and keep things safe even as you grow and expand.
Hide the WordPress version number
“Okay,” you might be saying, “what? How does this keep me secure?”
Well — it doesn’t, not directly. But if you’re a bit slow to update WordPress sometimes, a quick peek at your source code could easily tell a potential attacker that you’re potentially more vulnerable to other attacks. (Logic dictates that if you’re not staying up to date with WordPress, you might not be staying up to date with other things, so…)
The current version of WordPress can be found in three spots:
- The generator meta tag in your header
- The generator meta tag in your RSS feed
- Query strings
So, if you’re one of those well-meaning individuals who wants to test out your updates for a day or two and needs to hide the version number for a good reason, you can use Frankie Jarrett’s code to hide the version number from all three of these spots. Head over to his post to pick it up, then paste it into your functions.php file.

Again, hiding the version on its own will not protect you — you should absolutely keep WordPress, WooCommerce, and all of your plugins and extensions updated. But we also understand that there’s often a gap between testing and implementation, so this can help keep you safe in the interim.
Force SSL on your checkout pages
Security starts with a secure connection. By following this tip, you can be absolutely sure that you’re protecting your customers from spying eyes while they enter sensitive billing and shipping information at checkout.
With the “Force secure checkout” setting enabled in WooCommerce, all of the pages associated with your checkout process will be forced to use HTTPS (that is, a secure connection) every time they load.
Because only a customer’s browser and your store can decrypt the information being sent across a HTTPS connection, checking this box ensures that your checkout is safe, and that no one with malicious intent can take a peek at credit card numbers or other sensitive information flowing in and out of your store.
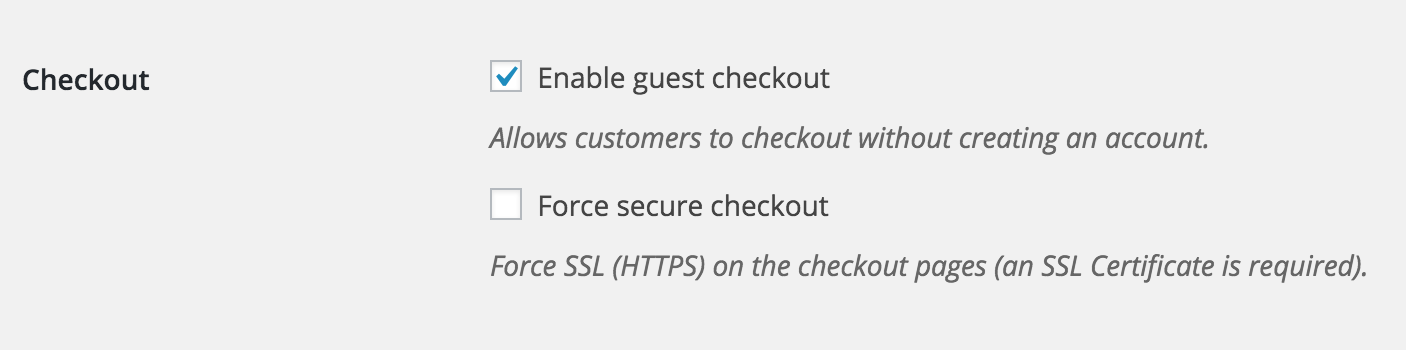
This setting can be toggled on and off in WooCommerce by going to WooCommerce > Checkout and toggling the second checkbox on or off.
Note that a valid SSL certificate is required for this setting to function properly on your store. If you haven’t yet acquired a SSL certificate, read this guide to learn more about why they matter and how to get one for little to no cost.
You can learn more about this setting in WooCommerce by reading this page in our docs.
Make backups and security scans a daily event
In our first post on security, we recommended using trusted software to scan your site for potential vulnerabilities, brute force attacks, or malware. Now that you’ve launched, it’s time to take things to the next level.
With your store up and running, both backups and security scans should be happening on a daily basis. Backups are crucial because they give you something to fall back on in the event of data loss, while security scans prevent such loss (or infection) from happening in the first place.
You can set the frequency of scans, backups, and notifications as you like, but we recommend a daily backup and a daily scan at the very least. Some solutions offer real-time backups and more frequent scans — Jetpack‘s brute-force login protection is real-time, too — but you can scale the frequency up or down as you prefer.
If you’re still in the market for a reliable, effective backup and security solution, VaultPress starts at just $9/month — and the first month is free for WooCommerce customers. Sign up here and get peace of mind from day one.
Change the default prefix used in your WordPress databases
Odd as it may seem, there are some nasty people out there who stage attacks on websites for their own amusement. While you might think your store is 100% safe, there are a few minor vulnerabilities that these spammers and hackers will find and exploit, given the chance.

One known potential vulnerability comes through the use of default database table settings during the setup and installation of WordPress. Changing these settings could help prevent malicious code from being injected into your server.
The default prefix for the database tables used to store WordPress information is wp_. Because most store owners don’t change this prefix during setup (or don’t even have the option to do so, depending on their host/installation procedure), using the default could put them at risk for a SQL injection attack (among others), all because hackers know full well what these default tables are named.
By now, of course, you’ve probably already set up WordPress and WooCommerce. But it’s not too late to change these settings. A SQL query or two run in phpMyAdmin will set you straight in no time.
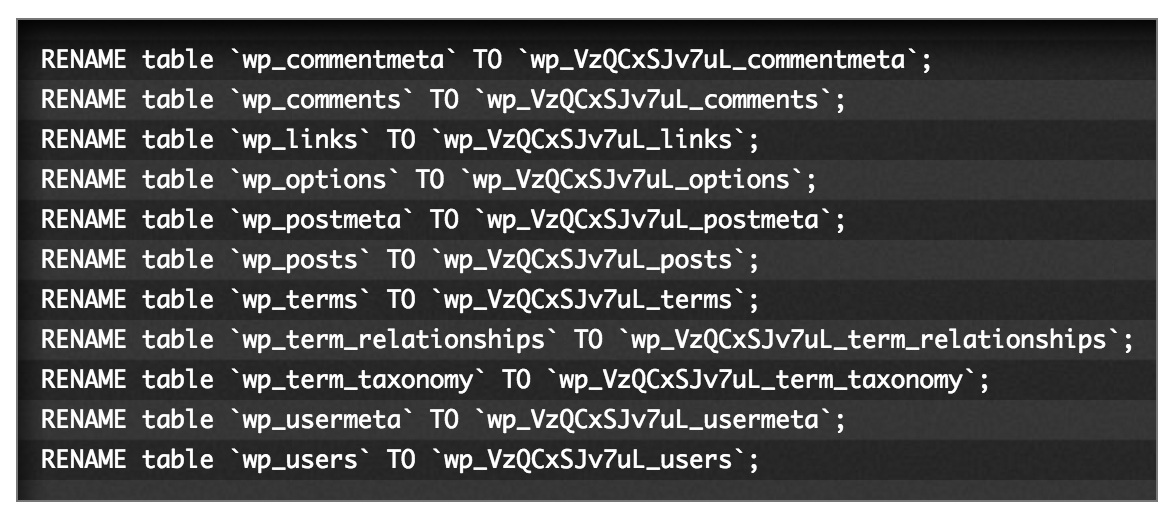
Have a look at this detailed and incredibly helpful step-by-step tutorial from Digging Into WP to learn how to change your database table prefixes to something far more complex — and far, far more secure.
SQL queries not your thing? There are a few free plugins around that will accomplish the same thing, but use caution — allowing unrestricted access to your SQL database can be dangerous. At the very least, uninstall a plugin like this once you’re done with it so there’s no potential for future unintentional renames.
Get rid of your “admin” account
This final piece of advice might seem annoying to some of you, or perhaps even like general knowledge to others. But it’s crucial, so we wanted to take the time to emphasize it here.
Using the default admin account built into WordPress is not recommended when you are running an online store. Much like the database table prefixes, hackers know this account (very likely) exists by default, which provides a better opportunity for them to brute force their way in.
Even similar-sounding accounts, like “testadmin,” “administrator,” or “owner” put your store at risk — they’re just as easily guessed. As the Attacking WordPress page on HackerTarget.com explains (don’t worry, it’s a resource for advice, not a how-to for hacking), once a hacker knows an account exists, they can quickly use a tool to guess your password:
[…]. 500 passwords were tested against the “testadmin” account (that was discovered during user enumeration). Those 500 passwords were tested in 1 minute and 16 seconds! While the test was running the site was still responding; a web server administrator would have no idea the attack took place without some sort of security log monitoring system in place.
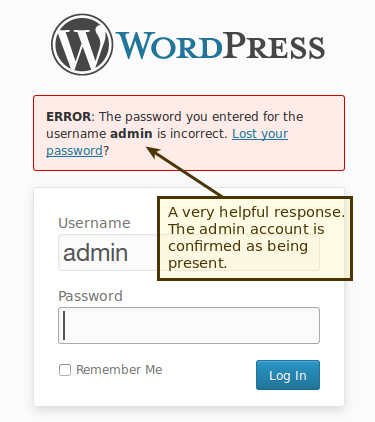
The moral of the story: your administrator account(s) should be named something unique and unlikely to be guessed by someone with malicious intent. Use a unique nickname, a full name with multiple initials in between, or something else that can’t be easily guessed (for example, your first and last name or the name of your store).
And remember to use secure passwords, so even if someone does guess the name of your account, they’ll still find themselves unable to log in. If you need a refresher on what’s secure and what’s not, see section #2 in this post.
Take security seriously once your store is online
Though there are plenty of things you can do to make a store secure before launch, security should be an ongoing concern for store owners — not a “one and done” thing. By following these tips and keeping your store and WordPress updated, you’ll be in a great position to keep your customers — and your team — safe and sound.
Have any questions about the security tips recommended in this post? Or better yet, any advanced tips of your own to share? We welcome your feedback and thoughts in the comments below.
Full acknowledgement of copyright source here: https://woocommerce.com/2016/04/woocommerce-security-post-launch/



