Banking Malware accounts for 41 percent of recorded malware attacks
In a recent report run by Action Fraud and the City of London Police, it has been found that Banking Malware accounts for 41 percent of recorded malware infections* in the UK.
Banking Malware is a type of software used by cyber criminals to target online bank accounts and allows them to obtain personal and financial details.
A computer or mobile device may become infected if it doesn’t have sufficient anti-virus protection, regular patches or software updates applied. Once infected, a cyber criminal can remotely take control of the internal functions of the device. With this they can start to steal personal data and access online bank accounts, encrypting files and distributing malware to other computers.
When a person gets malware on their computer there is normally a financial cost involved. This may involve having to buy anti-virus software products to protect the device or paying a ransom to regain valuable data and files. Or for businesses they may experience a loss in revenue from a Denial of Service attack (DDoS) on the company’s website.
Malware can be obtained from the ‘DarkWeb’ and can be downloaded either for free or purchased covertly by the cyber criminal. The price varies depending on the technical ability of the malware.
Computer users will unintentionally download malware by doing the following:
- Clicking on an infected file attachment in emails.
- Clicking on an infected website link.
- Clicking on an infected link whilst on a social media site.
- Inserting an infected removal drive into the computer.
- Downloading an infected file attachment on a text or via a mobile application.
Most Banking Malware steals information by following four different methods:
- Cookie Grabbers: cyber criminals steal information generated by the user whilst they are using the internet. This data may include banking passwords which then allow the criminal to access the user’s online bank account.
- Virtual Network Computing (VNC): When cyber criminals remotely access the device and infect it with the malware, this commonly happens when a user is using a public Wi-Fi network.
- Spy Modules: Allow the cyber criminals to observe web browser activities and the criminals are alerted when a user visits a specific website such as a banking website, which then allows them to make an attack.
- Drive Scanner: Is used by the criminals to search files and folders on the infected device and looks for documents with passwords or other useful information.
In a three month period the City of London Police was able to detect 280 different malware families, with banking malware accounting for 41 percent of all infections.
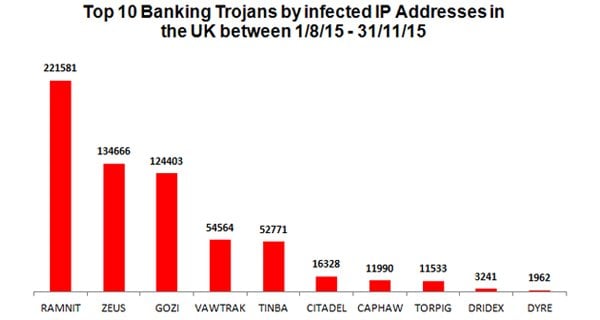
Ramnit is a type of Banking Malware that is most popularly used by cyber criminals. According to Symantec more than 3.2 million computers were infected globally over a five year period (2010-2015) by this type of malware. In February 2015 law enforcement and industry conducted an operation which led to a number of seizures of servers controlled by the Ramnit criminal group. However it is thought that it is starting to remerge and poses as a serious threat to all computer users.
This diagram shows the type of banking malware families which were most commonly used by cyber criminals in a 3 month period.
How to protect yourself from Banking Malware:
- Don’t click on links you receive in unsolicited emails or SMS messages. The links may lead to malicious website and any attachments could be infected with malware.
- Only install apps from official app stores, such as Google’s Play Store, or Apple’s App Store. Jailbreaking, rooting, or disabling any of the default security features on your mobile device may leave it more susceptible to malware infections.
- When logging in to your online banking account, be extremely cautious if you’re asked for details such as the 3 digit (CVV) number on back of your card, the long number on the front of the card, your card’s expiry date, or the 4 digit PIN for your card. If the online banking login page you’re on does ask for those details, then don’t login until you’ve called your bank to verify that you’re logging in to a genuine web page.
- Your bank will never ask you to transfer money out of your account and into another. Fraudsters will. If you receive messages, browser pop-ups or calls asking you to do this, then don’t respond to them. Call your bank immediately.
What to do if your computer has been infected with malware:
- You can disinfect you computer for free by using software from providers such as Microsoft and Symantec. The disinfection tools will identify whether a computer has been infected and, if so, disinfect it. The tool will cause no harm if used on computers that have not been infected.
- If your computer has been affected you should change all of your passwords on banking, email, social media and other potentially sensitive online accounts.
City of London Police’s Commander and National Coordinator for Economic Crime, Chris Greany said: “We live in an age where computers and mobile devices dominate our lives, both during work and play. Cyber criminals are increasingly using malware to access our financial details and are constantly adapting it so that they can try and get ahead of the security measures put in place by law enforcement and industry”.
“Both the public and businesses need to be aware of this and accept that whilst it is safe to use online banking; they should follow our protection advice which will help them to avoid their online bank accounts being compromised”.
*According to a report collated by Action Fraud and the City of London Police for date period: 1 September – 31 November 2015



